Cloud security is a top priority for businesses—especially when migrating sensitive data to the Cloud. The Atlassian Cloud is built on a foundation of robust security measures that protect data at every stage. This article explores how Atlassian secures its cloud platform by examining its security practices, data management processes, migration protocols, permissions management, auditing, and adherence to global standards. In other words, it’s a closer look at Atlassian Cloud security and what businesses can do to ensure compliance and data protection.
Keeping Data Secure
Physical Protection
Atlassian products and data are hosted on Amazon Web Services (AWS), a leader in Cloud hosting. The facilities, aka ‘data centers,’ are distributed across multiple regions and Availability Zones (AZs). The geographic distribution of data centers is the first line of defence. If one data center fails, the overall service will not be affected. Customers can choose their data residency (the geographic location of where the data is stored).
Moreover, data centers also have physical security measures such as round-the-clock surveillance, biometric access controls, and on-site security personnel to enhance Atlassian data security further.
Data is Encrypted
Data travels over public networks using industry-standard encryption protocols, which protect it from interception or unauthorized access. Customer data is safeguarded both in transit and at rest.
Once stored, advanced encryption techniques ensure the data remains confidential even if physical safeguards are breached. Specifically, Atlassian uses AWS Key Management Service (KMS). This ensures secure Atlassian access through reliable key management practices.
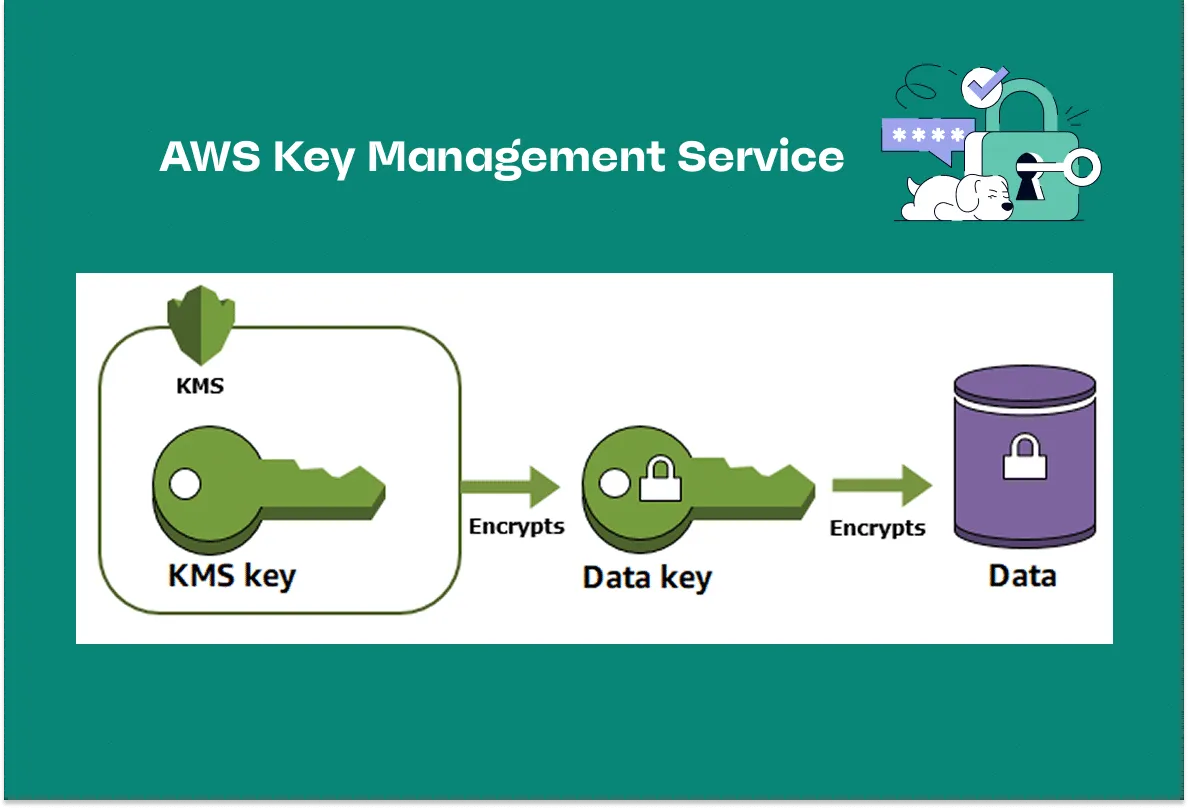
Source: AWS Developer Guide
In other words, imagine you have a treasure chest full of valuables (your data). Atlassian uses a service that works like a super-safe lockbox (AWS KMS) to manage the keys that open this chest. These keys are stored in a high-security vault (hardware security modules) that is inaccessible to even the lockbox managers.
Here’s the simple breakdown:
- Locking Your Valuables: Every time you store or send your valuables, a special key locks them away so only the right people (authorized services) can open the chest.
- Regular Key Changes: Just like you might change the lock on your door from time to time, these keys are regularly rotated to keep your treasure secure.
- Multiple Safes: The keys are managed in different locations, ensuring your chest is always safe and quick to access when needed.
Data is Unique - Tenant Context Service
A key concern IT managers might have is the multi-tenant Cloud environments. In other words, multiple customers’ data is stored in the same environment. However, Atlassian addresses this with its Tenant Context Service, where each customer is assigned a unique tenant ID.

Source: Atlassian
This logical segregation ensures that one organisation’s data remains completely isolated from that of another, providing reassurance to businesses with strict Atlassian cloud security requirements.
Securing Data During Migration
Migrating from on-premises or server-based systems to the Cloud requires meticulous attention to security. Atlassian employs secure communication channels that utilize HTTPS and other encryption protocols to ensure that data remains protected in transit. Strict access controls mean that only authorized roles, verified by active support tickets, can access customer instances during and after migration. These controls are reviewed on a quarterly basis to maintain strict oversight.
During migration, data may be temporarily stored in transit—sometimes for up to 14 days in certain regions and up to 30 days for some products. This data includes various elements, from automation rule configurations to product logs and user account information.
Extra Protection - Atlassian Guard
Besides strong encryption and access controls, Atlassian offers an extra layer of protection through Atlassian Guard. Atlassian Guard includes two cloud security products: Atlassian Access and Atlassian Beacon beta. Atlassian Access is Atlassian’s user management and authentication tool, while Atlassian Beacon mitigates risks to Cloud data with threat detection and response capabilities.
Atlassian Guard Premium plan comes with three major information security capabilities that some companies need before they can migrate to the secure Atlassian cloud:
- The ability to identify, classify, and remediate leakage of the most important data (e.g. PII, IP)
- Access to audit logs recording all user activity
- The ability to control the usage of API tokens and service/bot accounts
Migration Without the Internet
Moreover, Atlassian offers flexible migration methods for those with isolated production infrastructures. Organizations may choose two safe ways to move data out:
- Copying the system: making an identical duplicate in a building with internet access.
- Using a CSV file: transferring a detailed list of valuables using a secure spreadsheet.
Both options ensure migration can proceed securely, supporting Jira cloud security even in offline or restricted environments.
Compliance with Global Standards
Atlassian’s security framework is designed to meet a wide range of industry standards. By implementing an Information Security Management System (ISMS) in accordance with ISO 27001 and ISO/IEC 27018, Atlassian ensures that personally identifiable information is well-protected.
Compliance with PCI-DSS standards guarantees secure processing of credit card transactions, while adherence to the CSA STAR registry provides transparency in Atlassian data security controls. Additionally, SOC 2 certifications demonstrate the effectiveness of Atlassian’s operational and compliance controls. Atlassian’s FedRAMP compliance status is “In Process” as of the date of this article, with FedRAMP Moderate Authority to Operate coming soon. This highlights the company’s commitment to strong Jira cloud security compliance and standards for government agencies.
What You Can Do
Security in the Cloud is a shared responsibility. Atlassian implements stringent technical safeguards and physical protections, but organizations must also actively manage access, permissions, and overall governance. This collaborative approach ensures that data remains secure at every level, from day-to-day operations to complex migrations.
Organizations can enhance their security by verifying domains and centralizing user management. By confirming the authenticity of user accounts and consolidating access through tools like Atlassian Guard—which enforces two-factor authentication (2FA) and single sign-on (SSO)—companies simplify administration while strengthening Jira cloud security. Managing access permissions carefully is also critical.
Transform Your Business Securely
As organizations adopt cloud solutions, understanding and implementing these best practices becomes critical for maintaining Atlassian cloud security and operational integrity. Explore how the secure Atlassian cloud can revolutionize your operations with Seibert Solutions US. Get a free cloud migration quote now and unlock your organisation’s full potential for cloud performance.


